Surveillance Technology Helps Secure Border Zones
ADF STAFF
As Tunisia emerges from the most tumultuous period in its history, one thing has become clear: It must secure its borders.
This fact was illustrated during a bloody attack in March 2016 in which dozens of ISIS-aligned fighters entered the country from Libya, overran the border town of Ben Guerdan, and opened fire on police and Army buildings. After a gunbattle that lasted hours, more than 50 people lay dead, including 36 militants.
The incident grew even more disturbing when the attackers were identified, and most were found to be Tunisians. Some of the young men had grown up in the city they attacked.
As many as 7,000 young Tunisians have left the country to join extremist groups in recent years. As Libya has become lawless, traffickers in drugs, arms and people have crisscrossed the 459-kilometer border the two countries share.
“The Armed Forces and citizens must show vigilance, particularly in the face of the persistent crisis in Libya,” said Tunisian Minister of Defense Farhat Horchani during a tour of the border area. “The resolution of the crisis in Libya will allow Tunisia to secure its borders.”

“Border surveillance is the framework that supports our security system,” said Tunisian Minister of the Interior Hedi Majdoub.
Like Tunisia, other countries with porous borders are turning to technology. Although there is no simple solution, new low-cost technology is making it easier to gain an advantage over intruders and improve situational awareness at the border. Here are some tools that help:
Radar
Radar technology dates back to the 1930s. It works by producing electromagnetic radiation that flows out in waves. By tracking how these waves bounce off objects, the user sees a picture of the landscape. Ground-surveillance radar used at night can pinpoint the location of a person from a distance of 10 kilometers.
Radar is a valuable tool to build a complete picture of the border environment. It gathers information from 360 degrees, it can penetrate most weather conditions and it has a low latency period, which means it collects information quickly and it can monitor thousands of objects at once. Radar also is versatile. It can be placed on a tower or on a moving vehicle.
Some countries, including South Africa, are experimenting with mounting radar on aerostat blimps for wider coverage. A blimp flying at 1,500 meters can cover up to 150 kilometers for a month at a time, according to South Africa’s Council for Scientific and Industrial Research (CSIR).

In South Africa’s Kruger National Park, rangers use a wide area surveillance system known as the Meerkat to detect people and animals, particularly at night. Kenya also is using strategically deployed radar systems to monitor its troublesome border with Somalia.
Radar can be deployed in other unconventional ways. Ground-penetrating radar can find buried weapons or improvised explosive devices, and artillery-locating radar can track the locations of mortar rounds, rockets or missiles. Newer radar systems can penetrate the thick foliage of forests, which had previously posed a problem.
Satellites
Although many believe satellite technology is only available to wealthy nations, this is no longer the case. The cost of buying surveillance imagery from commercial satellites or launching a satellite has dropped greatly.
Walter Dorn, an expert on technology and peacekeeping, said high-resolution satellite imagery of a precision of 0.2 meters is now within the reach of many organizations and countries.
“The prices are falling, as are latency periods and delivery times, meaning that near real-time reconnaissance is now possible,” Dorn wrote in his paper “Smart Peacekeeping: Toward Tech-Enabled UN Operations.”
Small, off-the-shelf satellites known as “CubeSats” that are assembled from kits cost $10,000 or less.
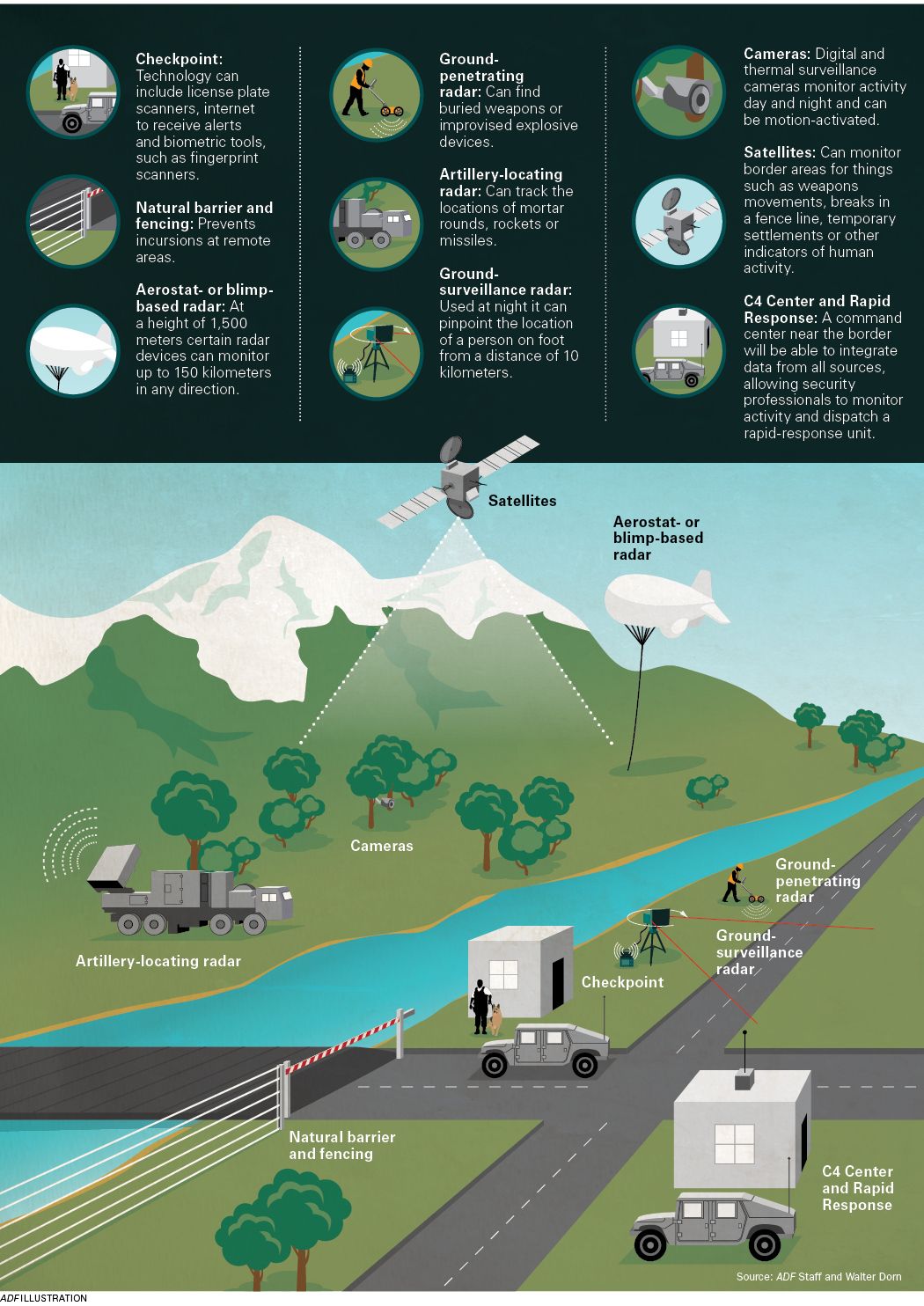 South Africa is one country taking advantage of this technology. It uses satellite surveillance to track migrants, poaching and trafficking, particularly near its border with Zimbabwe. Although a satellite may only pass over an area once or twice per day, it can help security professionals identify things such as walking paths, breaks in a fence line, temporary settlements or other indicators of human activity.
South Africa is one country taking advantage of this technology. It uses satellite surveillance to track migrants, poaching and trafficking, particularly near its border with Zimbabwe. Although a satellite may only pass over an area once or twice per day, it can help security professionals identify things such as walking paths, breaks in a fence line, temporary settlements or other indicators of human activity.
Additionally, programs can use geographic information systems to overlay images from other sources, including positioned cameras or crowdsourced photos. “Such data fusion can help give advance warning of attacks or rebel movements across the borders with neighboring countries,” Dorn wrote.
Cameras and Sensors
In recent years, digital surveillance cameras have become lighter and cheaper, while offering higher resolution. Remote video surveillance systems on towers or mobile platforms can send video to a control room so agents can track or identify suspicious figures in a border zone.
Many cameras also are being paired with sensors to track motion, acoustic activity or seismic sensors used to monitor explosives. Perhaps most exciting is the increasing availability of sensors that can monitor the spectrum of light that is invisible to the human eye. The infrared light, which includes heat or thermal radiation, enables night vision. Like other technology that once was the exclusive domain of the military, thermal imaging cameras are becoming mainstream.
“Breaking the night barrier is essential,” Dorn wrote. “Because many nefarious activities in war-torn areas are done using the cover of darkness, including attacks (or preparations for dawn attacks) and smuggling of illicit arms and human beings. Since many atrocities are committed at night, peacekeeping cannot be a daytime-only job.”
Integration
When using different tools to monitor borders, it’s important to integrate data to form a complete operating picture. “These are systems of systems,” said Dr. Thomas Jacob, who served as the vice president in charge of border security and integrated systems at Airbus. “It’s not just sensors. You have to integrate a lot of systems.”
When this integration is done effectively, a command, control, communications and computer (C4) center near the border will be able to monitor all activity and dispatch a rapid response unit to investigate anything suspicious.
This “becomes the nerve center of a mission where various sources are integrated into a single comprehensive view,” according to a CSIR paper on surveillance technology. “Information from diverse systems such as radar, satellites and video feeds from unmanned aerial telemetry systems, communication devices and others can be displayed on screens to provide an integrated overview of a defence scenario.”
By building a full picture of the border and identifying areas of weakness or concern, security professionals are better able to use their limited resources. By targeting these weak spots, they can close the gaps in their coverage.
The buildings should have different security equipment to keep everyone secured.
Check some useful technology, you can check and look at more info – SecurityInfo
“This means improved surveillance — without sending armies of patrol staff — and the information as a deterrence mechanism or best-suited combat tactics is available to commanders,” the CSIR paper states. “Combining various surveillance and detection technologies in integrated communication and command systems [improves] the ability to watch over the country’s territories.”


Comments are closed.